Every year new cybersecurity technologies, vendors and solutions emerge — yet breaches continue to hit the headlines. Organisations have scrambled to develop a better security posture, but the dizzying array of options leaves resource-constrained IT and security leaders wondering how to proceed.
Creative ITC is a multi-award-winning cloud services provider with a successful track record of delivering game-changing technology solutions to some of the world’s leading businesses. We’ve partnered with global security leader, Arctic Wolf, to help you find the right security solution for your organisation.
Follow our at-a-glance comparison of cybersecurity solutions to help you find the right combination of technology, features and people to help you stay ahead of today’s evolving threat landscape.
Cybersecurity Solutions
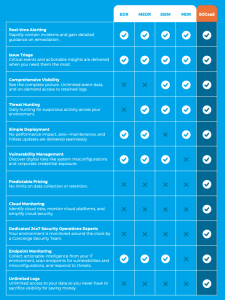
There are 5 main options within the cybersecurity solution landscape. They are split between DIY and Managed options.
DIY Options
EDR
EDR stands for Endpoint Detection and Response. It protects endpoints, but still requires the right people and process to operate.
SIEM
SIEM (Security, Information and Event Management) collects security data from network devices. To function efficiently, you need a team with various skillsets.
MEDR
MEDR stands for Managed Endpoint Detection and Response. It only covers endpoints, leaving vulnerabilities within your organisation.
MDR
Managed Detection and Response has a capabilities range across vendors. It correlates host and network data for threat detection and incident investigation.
SOCaaS
SOCaaS, also known as Security Operations Centre as a Service, combines people, process and technology for 24×7 monitoring across network endpoints and the cloud.
What Cybersecurity Measures Does My Business Need
The Benefits Of Creative ITC’s SOCaaS
The Artic Wolf Platform
Processing over 200 billion events per day, driving faster threat detection, simplifying incident response and eliminating alert fatigue.
Concierge Security Team (CST)
Continuously monitoring security events enriched and analysed by the Artic Wolf Platform. Improving your overall security posture.
Predictable Pricing
No limits placed on data collection. The more data we collect and store on your behalf, the better we are at bolstering you’re your security posture.
Core Technology Ownership
We control our entire technology stack and roadmap – delivering functionality faster for our customers.
Strategic Guidance
Leveraging their security expertise combined with knowledge of your environment, CSTs introduce ways to improve your posture along your security journey.
Broad Visibility and Coverage
Providing enhanced visibility on-premises (endpoint, network, any log source) as well as cloud (SaaS, IaaS).
Get in touch with Creative today to discuss your cybersecurity strategy.